Compromising Two Factor Authentication on Gmail
Social Engineering: Compromising Two Factor Authentication on Gmail
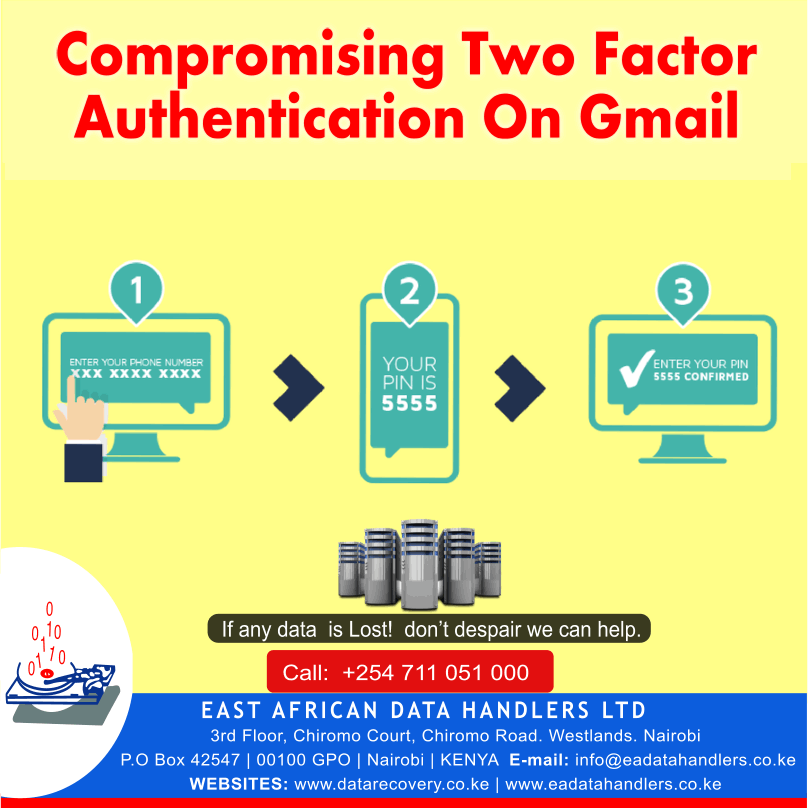
Two factor authentication just like many other security controls is perceived as a good security control. Many companies establish these controls within their organizations and at the same time hackers who wish to access company data are constantly trying to find ways to beat these controls. Sometimes they fail to find ways through these control so they decide to “hack the employees” this is basically termed as social engineering. This info graphic shows how a human resource manager was tricked into letting the hacker log into his Gmail.
In the Kenya Cyber Security Report 2016, one of the cyber security Gaps in Kenya is employee training, many companies install great security controls but don’t give any sort of training to the employees who consequently expose the companies to hackers.
Demonstration
Contact us now
If you’ve lost valuable, irreplaceable mobile data or need Data Recovery Plan for your Oraganisation or business— We can save it! Call us now at +254 711 051 000 or visit our offices Chiromo Court 3rd Floor Westlands, Kenya. Best of it, we have distributed offices all over East Africa and can easily get your device brought to us from anywhere in East Africa.
Also we have other services in data recovery for various devices; Hard Drives, Laptops, Desktops, Raid Systems, RAID / NAS / SAN , Servers, Memory Cards, Flash Drives, Databases, SSD Drives etc
East African Data Handlers ltd no data – no charge policy means you owe us nothing if we are unable to recover your critical files.