Suicide of two people after Dating Site Hacking done!
Courtesy of (Alastair Sharp) (a Yahoo News Uk Writer )
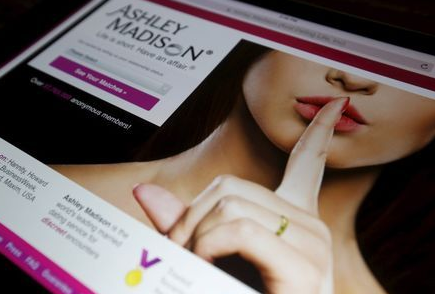
TORONTO (Reuters) – At least two people may have committed suicide following the hacking of the Ashley Madison cheating website, Toronto police said on Monday, warning of a ripple effect that includes scams and extortion of clients desperate to stop the exposure of their infidelity.
Avid Life Media Inc, the parent company of the website, is offering a C$500,000 ($379,132) reward to catch the hackers.
In addition to the exposure of the Ashley Madison accounts of as many as 37 million users, the attack on the dating website for married people has sparked extortion attempts and at least two unconfirmed suicides, Toronto Police Acting Staff Superintendent Bryce Evans told a news conference.
The data dump contained email addresses of U.S. government officials, UK civil servants, and workers at European and North American corporations, taking already deep-seated fears about Internet security and data protection to a new level.
“Your actions are illegal and will not be tolerated. This is your wake-up call,” Evans said, addressing the so-called “Impact Team” hackers directly during the news conference.
“To the hacking community who engage in discussions on the dark web and who no doubt have information that could assist this investigation, we’re also appealing to you to do the right thing,” Evans said. “You know the Impact Team has crossed the line. Do the right thing and reach out to us.”
Police declined to provide any more details on the apparent suicides, saying they received unconfirmed reports on Monday morning.
“The social impact behind this (hacking) – we’re talking about families. We’re talking about their children, we’re talking about their wives, we’re talking about their male partners,” Evans told reporters.
“It’s going to have impacts on their lives. We’re now going to have hate crimes that are a result of this. There are so many things that are happening. The reality is … this is not the fun and games that has been portrayed.”
The investigation into the hacking has broadened to include international law enforcement, with the U.S. Department of Homeland Security joining last week. The U.S. Federal Bureau of Investigation and Canadian federal and provincial police are also assisting.
Evans also said the hacking has spawned online scams that fraudulently claim to be able to protect Ashley Madison clients’ data for a fee.
People are also attempting to extort Ashley Madison clients by threatening to send evidence of their membership directly to friends, family or colleagues, Evans said.
In a sign of Ashley Madison’s deepening woes following the breach, lawyers last week launched a class-action lawsuit seeking some $760 million in damages on behalf of Canadians whose information was leaked.
Evans said Avid Life first became aware of the breach on July 12, when several employees booted up their computers and received a message from the infiltrators accompanied by the playing of rock group AC/DC’s “Thunderstruck.”
The company went to police several days later, he said, while the hackers went public on July 20.
(Reporting by Alastair Sharp and Andrea Hopkins; Editing by Jeffrey Benkoe)