Ransomware Recovery Services.
Are you someone who has been infected by a ransomware? Did you know we do ransomware recovery services? Ransomware attacks are continuing to evolve, both in sophistication and numbers. At East African Data Handlers our security experts can help you with ransomware data recovery services. We have the skills to recover your data back to its original readable form.
So what is Ransomware?
Ransomware is a subset of malware in which the data on a victim’s computer is locked, typically by encryption, and payment is demanded before the ransomed data is decrypted and access returned to the victim. The motive for ransomware attacks is nearly always monetary, and unlike other types of attacks, the victim is usually notified that an exploit has occurred and is given instructions for how to recover from the attack. Payment is often demanded in a virtual currency, such as bitcoin, so that the cybercriminal’s identity isn’t known.
East African Data Handlers Data recovery Engineers have the expertise to recover encrypted media and files. We use the best practices for data security protocols to ensure data privacy through all stages of recovery process.
Ransomware attacks are a growing problem for computer users and server administrators. The FBI received 2,500 ransomware complaints in 2015, and each instance of ransomware infection can easily result in thousands of dollars of damages.
For the last four years, we have recovered data for ransomware victims, but recently, we have begun to receive an influx of new cases. The threat will only grow in this 20th century , which is why East African Data Handlers now offers specialized services for ransomware recovery and decryption.
You need fast access to your files, but immediately paying the ransomware creator is not a safe or effective option. Call 0711 051 000 today to speak with a malware expert or read on to understand your options.
Types of Ransomware and Data Recovery Options
Ransomware or cryptovirus is a malicious program that blocks access to data by encrypting the victim’s media. It then presents the user with a message, asking for money (usually via a digital currency such as Bitcoin). Unless the victim pays, the data will remain permanently encrypted.Media not encrypted
Examples of ransomware include the following and their variants:
- GandCrab Ransomware Now updated to .CRAB Virus (GANDCRAB V2.1 Ransomware)
- SamSam
- Cerber
- Crysis
- CrypMIC
- Locky
- HDDCryptor
- Merry X-Mas
- CryptXXX
- CryptoWall
- CryptoLocker
- TorrentLocker
- KeRanger
- Bart
- Zepto
- Jigsaw
The good news is that some ransomware programs use outdated encryption, some of the encryption techniques have been broken, and some keys and source code have been recovered (often after the creator is arrested) enabling decryption. However, in many cases, ransomware encryption is unbreakable.
If your computer is infected with ransomware, East African Data Handlers can help you restore the affected data. As one of the world’s top data recovery companies, we can assist malware victims in several ways:
- Determine Recoverability – In many instances, data is recoverable via an alternative method. Our engineers will assess your unique situation to determine the safest and most cost-effective option for restoring your important files.
- Data Decryption – We can determine whether a decryption key exists for your ransomware infection or if one can be created. If decryption is feasible, we can perform the process safely, returning your systems to a functional state.
- Ransom Management – As a last resort, if you are forced to pay the ransom, we can help you obtain bitcoin and manage the process without providing the malware creator with your personal information. This can also simplify accounting when businesses are affected with ransomware.
Paying the ransom is always a last resort, but we leave it open as an option because our goal is to restore your files under any circumstances. As every case is different, we cannot guarantee that a decryption method exists for your case without performing an evaluation.
How is Ransomware Installed On My Computer?
Ransomware is installed on your system when you open an infected file. Executables (.exe extension on Windows computers), or files with some sort of execution method, are the most susceptible. For example a Word document (.doc or .docx) may run a macro that allows the cryptovirus to start its process.
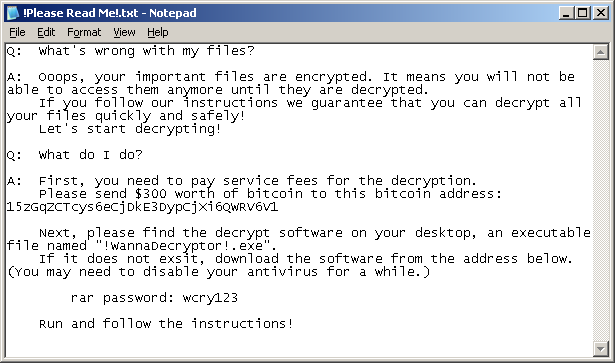
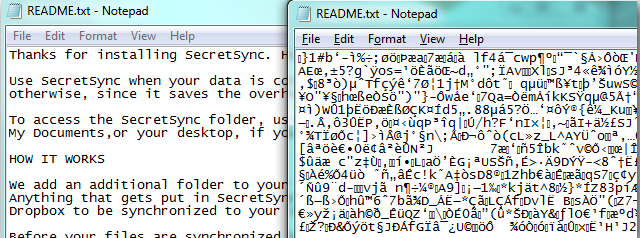
Below is a list of ransom note files.
_HELP_instructions.html
_how_recover.txt
_Locky_recover_instructions.txt
About_Files.txt
Coin.Locker.txt _secret_code.txt
DECRYPT_INSTRUCTION.TXT
de_crypt_readme.bmp
de_crypt_readme.txt
de_crypt_readme.html
DECRYPT_ReadMe.TXT
DecryptAllFiles.txt
DECRYPT_INSTRUCTIONS.TXT
DecryptAllFiles.txt
encryptor_raas_readme_liesmich.txt
FILESAREGONE.TXT
help_decrypt_your_files.html
HELP_TO_SAVE_FILES.txt
Help_Decrypt.txt
HELP_RECOVER_FILES.txt
help_recover_instructions+[random].txt
HELP_RESTORE_FILES.txt
HELP_TO_DECRYPT_YOUR_FILES.txt
HELP_TO_SAVE_FILES.txt
HELP_YOUR_FILES.TXT
HELLOTHERE.TXT
HELPDECRYPT.TXT
HELPDECYPRT_YOUR_FILES.HTML
HOW_TO_DECRYPT_FILES.TXT
How_To_Recover_Files.txt
howrecover+[random].txt
howto_recover_file.txt
Howto_Restore_FILES.TXT
HowtoRestore_FILES.txt
IAMREADYTOPAY.TXT
IHAVEYOURSECRET.KEY
INSTRUCCIONES_DESCIFRADO.TXT
Read.txt
ReadDecryptFilesHere.txt
ReadMe.txt
README_FOR_DECRYPT.txt
READTHISNOW!!!.TXT
recover.txt
recoverfile[random].txt
recoveryfile[random].txt
RECOVERY_FILE.TXT
RECOVERY_FILE[random].txt
HowtoRESTORE_FILES.txt
RECOVERY_FILES.txt
RECOVERY_KEY.txt
recoveryfile[random].txt
restorefiles.txt
SECRET.KEY
SECRETIDHERE.KEY
YOUR_FILES.HTML
YOUR_FILES.url
This is a partial list of files, and it may not be completely up to date. If you believe that you have a ransomware-infected file, do not open it. Call us or send us an email ( info@datarecovery.co.ke ) to discuss your next steps toward safe recovery.
For Ransomware Data Recovery Service , get a real deal with real experts call us on 0711051 000